As of August 2016, the world population was estimated at 7.4 billion. Of those, an estimated 3 billion are internet users. And as of today, 1 out of 3 of those users are likely to have been impacted by the largest cyberattack of all-time.
Yes, you did your math right. Yahoo announced on Wednesday that 1 billion of their user accounts were compromised. Now, you may be thinking to yourself “didn’t I read somewhere about a data breach with Yahoo earlier this year?” and you’d be right! Yahoo announced back in late September 2016 that they were hacked and that over 500 million of their users account data were stolen. The craziest part of this story? Not only was today’s announcement separate from September’s… it is very likely to have been committed by two different groups.
Now, when you take a step back and look at the headline-making cyberattacks of the past few years (e.g. Home Depot, Target, Sony, U.S. federal government through the Office of Personnel Management, and most recently publicized, the Democratic National Committee) you start to see a trend: organizations not investing enough resources in securing their networks and digital infrastructure. The reasoning could be as simple as they don’t know they need to, they don’t think they can prioritize in their budget, or they don’t think a hack will happen to them. Yahoo clearly made some or all of these mistakes.
While you may be thinking that only the largest companies, governments, and political organizations are at risk, statistics tell a very sobering story. According to the U.S. Small Business Association, nearly half of U.S. small businesses will be the victim of a cyberattack with an average cost of an estimated $21,000 (not including additional damage from lost customer trust). PwC’s annual Global Economic Crime Survey also showed that cybercrime has not climbed to the 2nd most reported economic crime affecting organizations.
The reality is every organization, small and large, needs to shift their security strategy from “if to when” and take the necessary steps to safeguard their users, devices, apps, and data. Considering 63% of confirmed data breaches involve weak, default, or stolen passwords, a great first step is reevaluating how to consolidate and safeguard your employee’s digital identity.
With Microsoft’s Enterprise Mobility + Security suite, you are able to do some incredibly powerful things very cost-effectively. An example I’ll provide today is around securing your employee’s identity (credentials) using the included Azure AD Premium and Intune products. By using your organization’s existing investments in Microsoft Active Directory, we are able to deploy a small tool to synchronize your existing user objects and attributes to Microsoft’s Azure Active Directory platform and then provide single sign-on to (SSO) to all of your cloud-based (SaaS) and on-premise applications. I think we can all agree a single username and password to remember is better for everybody.
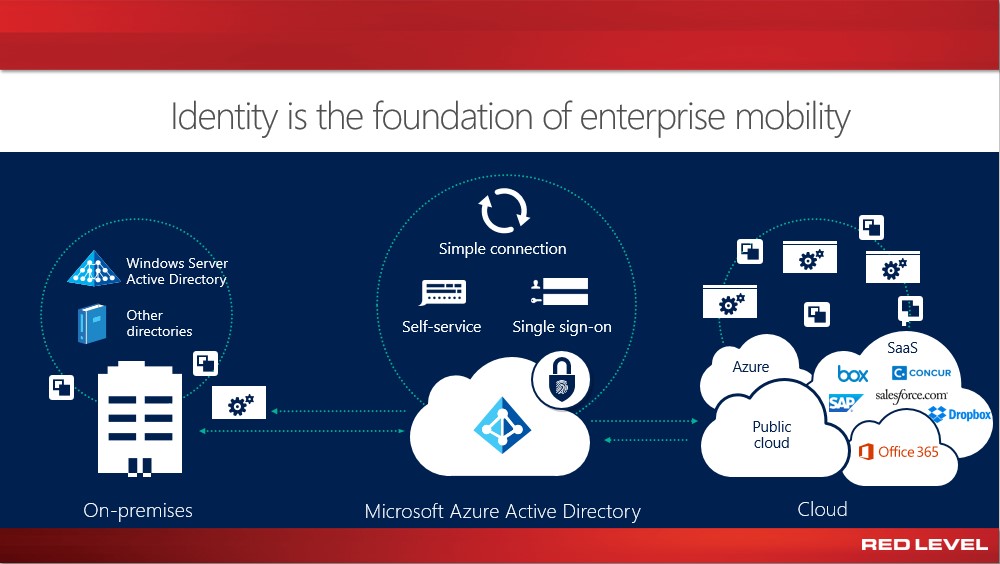
While SSO is great for reducing the amount of credentials that could be compromised while enabling a much better user experience, it still isn’t enough. Most of us are familiar with multi-factor authentication (MFA) through online banking (the phone call, text, or email to confirm you are who you say you are) but even MFA isn’t going to cut it anymore. To provide an exceptionally strong defense against attacks on your employee’s identity, let me introduce you to conditional access (CA). With CA implemented properly, you now have a rich set of variables (some examples listed in the image below) that must be met for someone to access your organization’s cloud and on-premise applications and data.
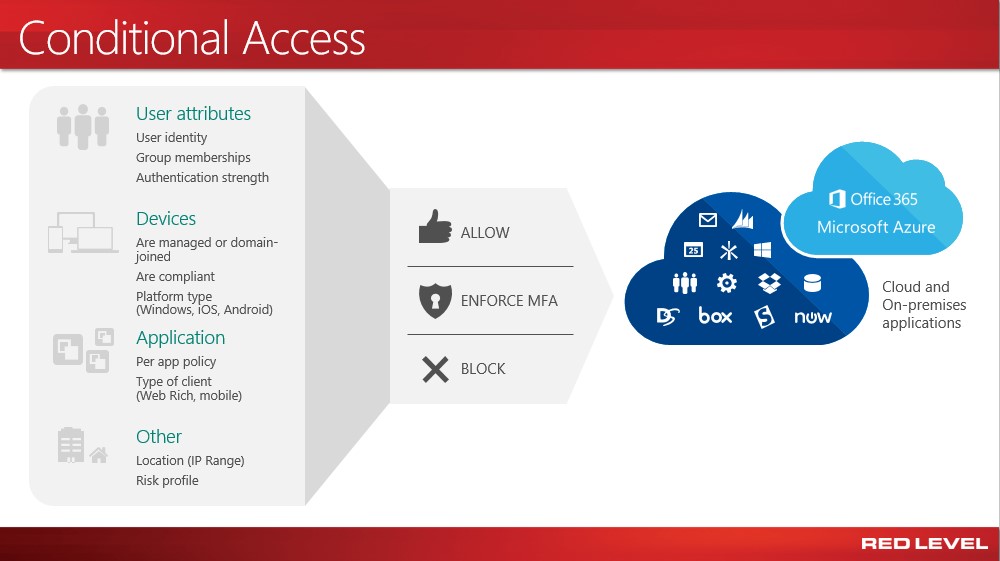
My favorite part of CA is providing the functionality so you can set multiple variables to be met to allow streamlined access directly to the intended resource while forcing a MFA request if only some of the variables have been met. If some non-negotiable variables you set don’t pass validation, you can simply block access.
Leveraging Microsoft’s machine learning and massive set of data (about 14 billion daily authentication events each day in addition to other information), you can also look at the risk profile on the request and provide some automated intelligence to the equation. A great example of this is the “impossible travel” risk event. It is exactly what it sounds like: the system identifies two sign-ins originating from geographically distant locations, where at least one of the locations may also be atypical for the user, given past behavior. In addition, the time between the two sign-ins is shorter than the time it would have taken the user to travel from the first location to the second, indicating that a different user is using the same credentials.
I’ve only scratched the surface of what is possible with Microsoft’s Enterprise Mobility + Security suite but invite you to email ems@redlevelnetworks.com for a FREE cybersecurity workshop. It is a one-day on-site business and technical workshop featuring all the products in the EMS suite delivered by Red Level’s team of security consultants. We’ll also develop an analysis report with our findings, areas impacted, identified value, and our recommendations.
Have questions or feedback? Let me know by leaving a comment below. Thanks for reading and stay safe out there!
For more information about gaining a competitive advantage with digital transformation, contact Red Level today.
Related Posts
Data breaches have become all too common, and the recent ...
What you do on autopilot can hurt you – especially ...
The threat landscape is becoming more incessant, dangerous, and high stakes for businesses. The sheer quantity of attacks has ...