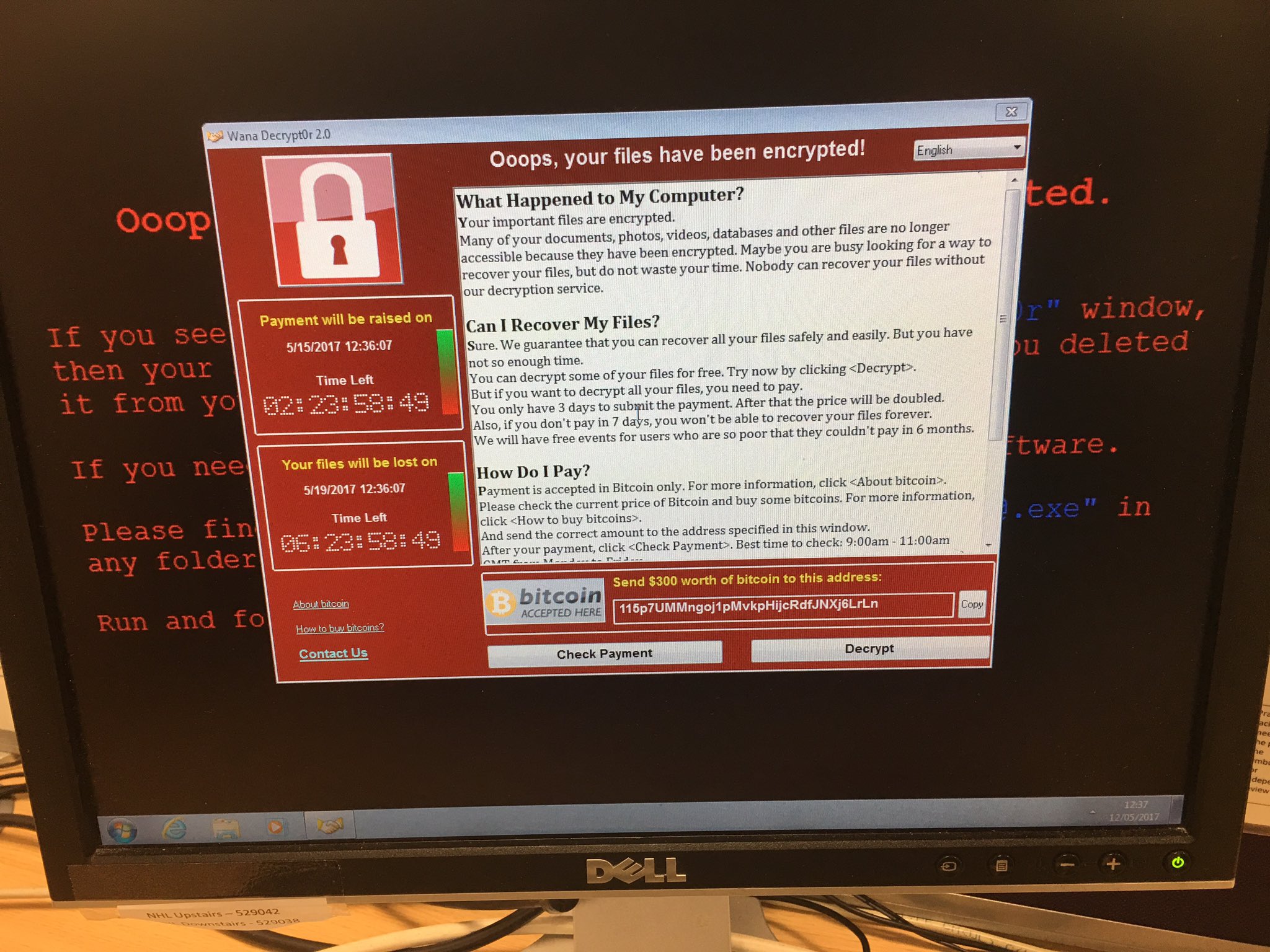
April Showers Brings May Security By Avoiding Attacks
The cyber security threat landscape is evolving, most companies’ solutions are not solving these attacks. Attackers are spending more than 287 days on average in companies they breach – and the amount of damage done in that time is astonishing. Three-quarters of those breaches are directly linked to the mismanagement or theft of user credentials. What is most alarming is that companies’ solutions cannot solve the problem. Expect breaches to happen, instead of struggling to protect your business from outside threats. So what can you do? Rely on detection and containment to best secure your environment. What if your employees need to access information from outside the office and often from their own devices? More importantly, how do you ensure that your data stays safe and out of the reach of likely attacks? One recommendation is to rate your mobility landscape. One question to ask yourself is, “How well am ...