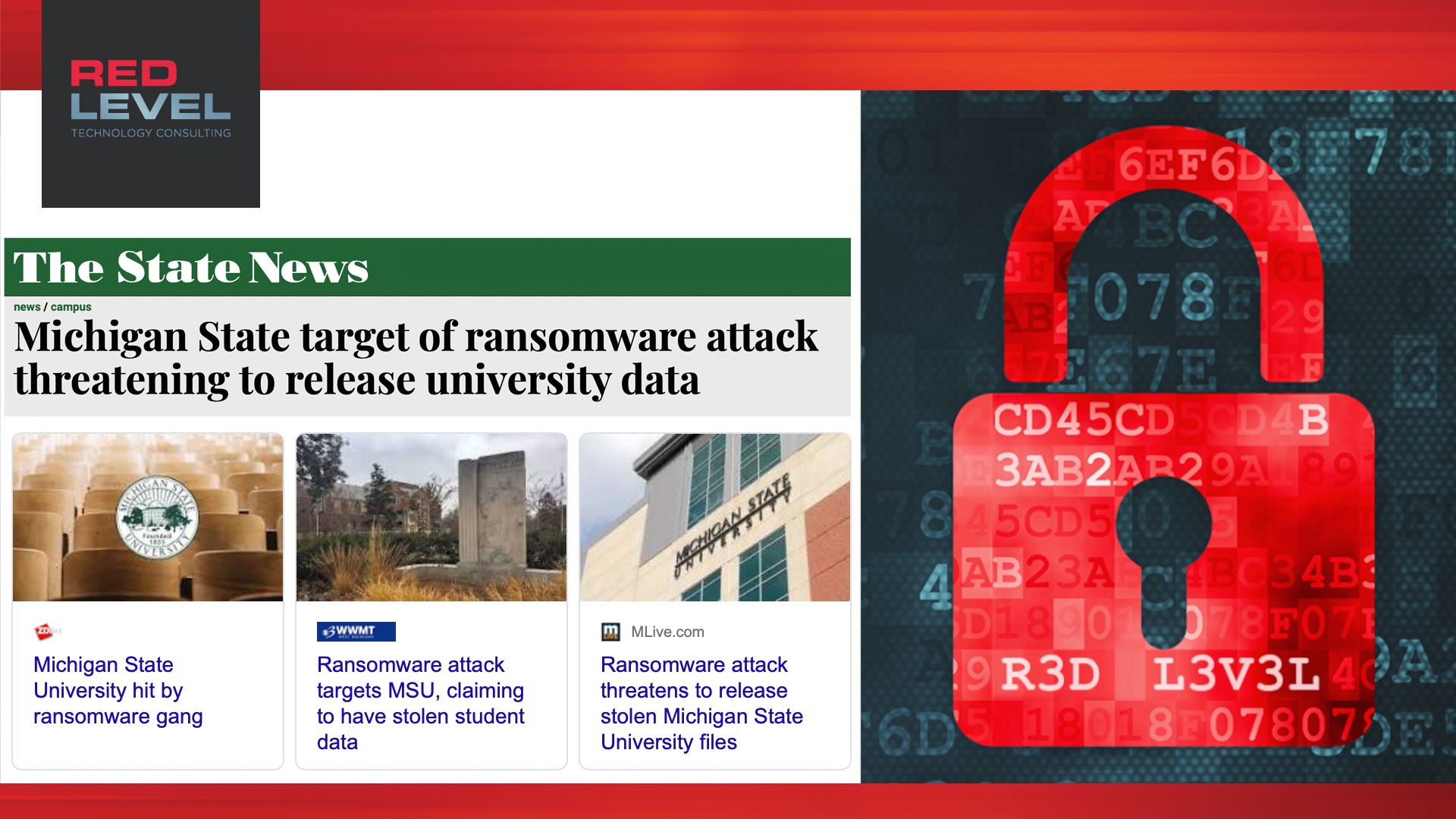
While we’re all focused on working through COVID in the real world, hackers are working their nefarious scams in the virtual world. Their latest target is close to home – Michigan State University.
A ransomware attack infected MSU yesterday stealing student data, files, and financial information.
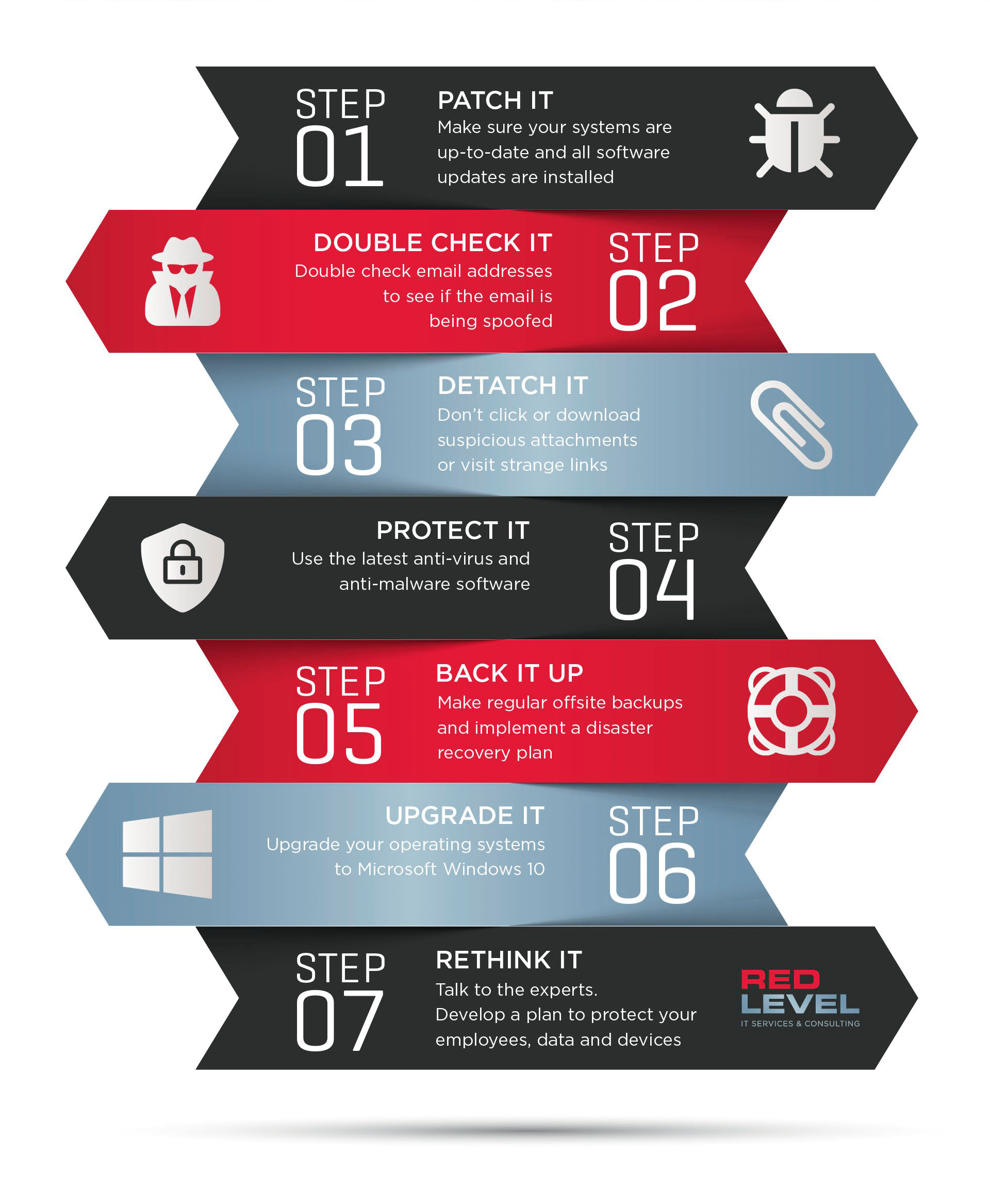
Red Level has solutions to protect your clients, data, and reputation, but there are also several simple things you can do to stay safe:
- Apply patches and updates. Ensure that systems are up to date and that all software updates are installed.
- Double-check email addresses. Watch for unfamiliar names and domains, as well as ‘spoofed’ accounts pretending to be trusted contacts.
- Think before clicking. Don’t click or download suspicious or unexpected attachments, or visit unfamiliar links.
- Use proactive protection. Install and use the latest antivirus and anti-malware software available.
- Keep regular backups. Maintain a regular offsite backup schedule and implement a disaster recovery plan.
- Modernize your server. Upgrade server operating systems to Windows Enterprise Server.
- Talk to us. Red Level can develop a comprehensive plan to protect your users, customers, systems, and data.
Red Level’s Ed Aube and Robert J Tessanne Jr share 7 quick tips for protecting your business and organization from Ransomware attacks in this video.
Here’s a handy infographic with the 7 tips. Print one up for the break room to remind your team how to avoid a ransomware attack at your organization.
As always, if you’re concerned about the safety of your data, contact Red Level to speak with one of our technology consultants. Let us know more about your company’s needs, and we’ll show you how Red Level can help.
For more information about gaining a competitive advantage with digital transformation, contact Red Level today.
Related Posts
Data breaches are becoming alarmingly common. The recent "Mother of ...
What you do on autopilot can hurt you – especially ...
Looking for a leg up on your competitors? Making sure ...