Office 365 Exchange Online is a robust email platform, but it’s still vulnerable to cyber-attacks. One such attack is spoofing. Spoofing is when somebody with malicious intent sends an email to trick you into thinking that the email is coming from someone you know within your organization or someone you receive emails from regularly. For example, I received one last week from someone that appeared to be from Amazon for Business the email was telling me to reset my password to click to verify and asking me to put in my credentials. It looked very similar to an Amazon email. It had the Amazon logo, and the form was professionally done. However, I do not have an Amazon for Business account, so I knew it was a spoofing attempt.
Here are a couple of examples of what you might see when someone has sent you a spoofed message:
- The display name may say Microsoft Outlook and have a domain that is similar to Outlook. On mobile, you need to be more aware because it does not always show the email address, just the display name.
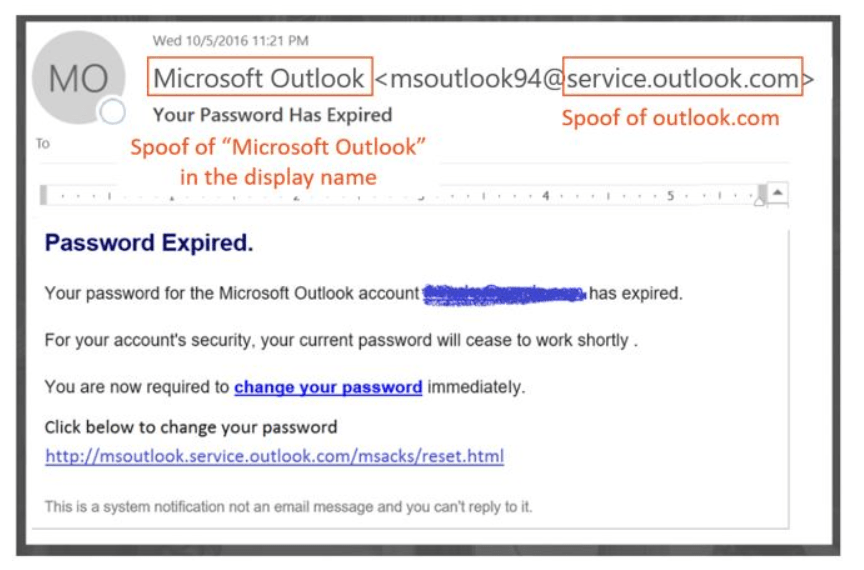
- The spoofer may have researched you on LinkedIn to find out who your boss is, they may send you an email that looks like it is coming from your boss asking you to transfer money or pay an invoice.
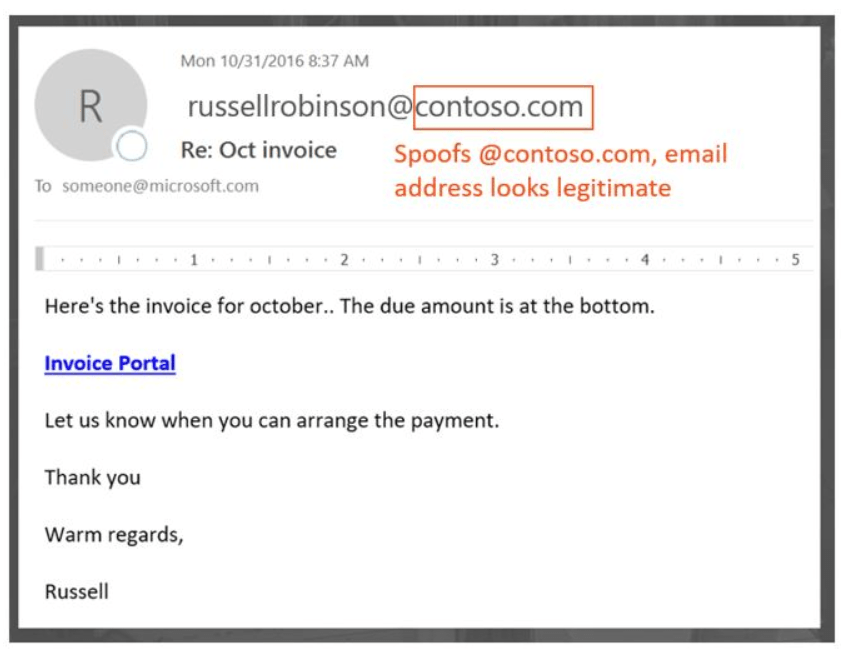
Always check the sender’s email address. If you see something that might look a little off, make sure that the domain is the sender’s actual domain. However, spoofing is becoming more advanced, and attackers now have the ability to spoof the domain.
What can you do?
There are three ways that you can protect yourself:
- Set up Sender Policy Framework (SPF) records. These are public domain records that identify your mail server. If I send an email to someone, their email server is going to look at the domain and check my SPF record and the IP that the message came from and determine whether or not the email is from my authorized servers. If the SPF records and IP don’t match what I had set up, Office 365 will block the email or put in in quarantine.
- Configure DomainKeys Identified Mail (DKIM). DKIM is a digital signature that is attached to the email message. When the recipient gets the email, Office 365 will look at the signature and check your public DKIM records and make sure that they match up and that it is authenticated. If it does not match, it can still be delivered but may go into their Spam or Junk folder.
- Validate with Domain-based Message Authentication, Reporting, and Conformance (DMARC). DMARC uses SPF and DKIM together. It will check the SPF record of the mail and the DKIM to make sure everything matches. If everything matches, the message will be delivered. If they don’t, you can set your DKIM or DMARC to either reject it or put it in quarantine.
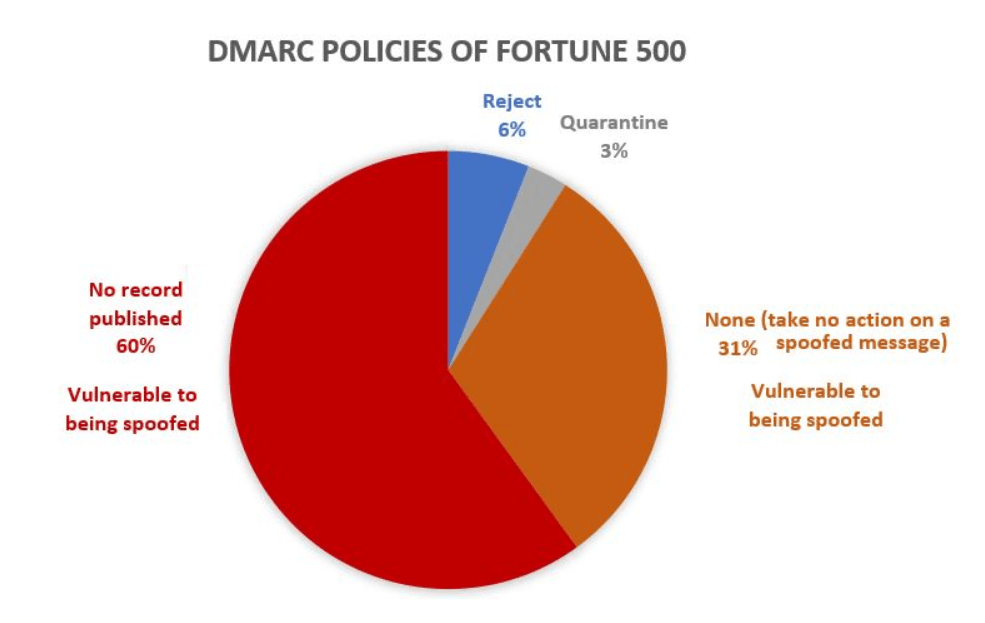
Here is a graph that shows the DMARC Policies of Fortune 500 companies. As of March 2018, only 9% of domains of companies in the Fortune 500 publish strong email authentication policies. The remaining 91% may be spoofed by a phisher, and unless the email filter detects it using another policy, it may be delivered to an unsuspecting end-user.
If you have Office 365, there are some built-in protections, but you’re still vulnerable. Red Level can help you set up, configure, and validate your domain to protect you from future spoofing attacks with our Microsoft Security Assessment.
For more information about gaining a competitive advantage with digital transformation, contact Red Level today.
Related Posts
Windows 10 End of Support is Coming Microsoft is officially ...
Microsoft is enhancing SharePoint to help organizations create more engaging ...
Microsoft is enhancing SharePoint to help organizations create more engaging ...