As we move into a cloud-first world, identity protection is becoming more necessary and prevalent. A cloud-first world has a lot of benefits, but it also comes with its challenges.
Identity Challenges for Today’s Organizations
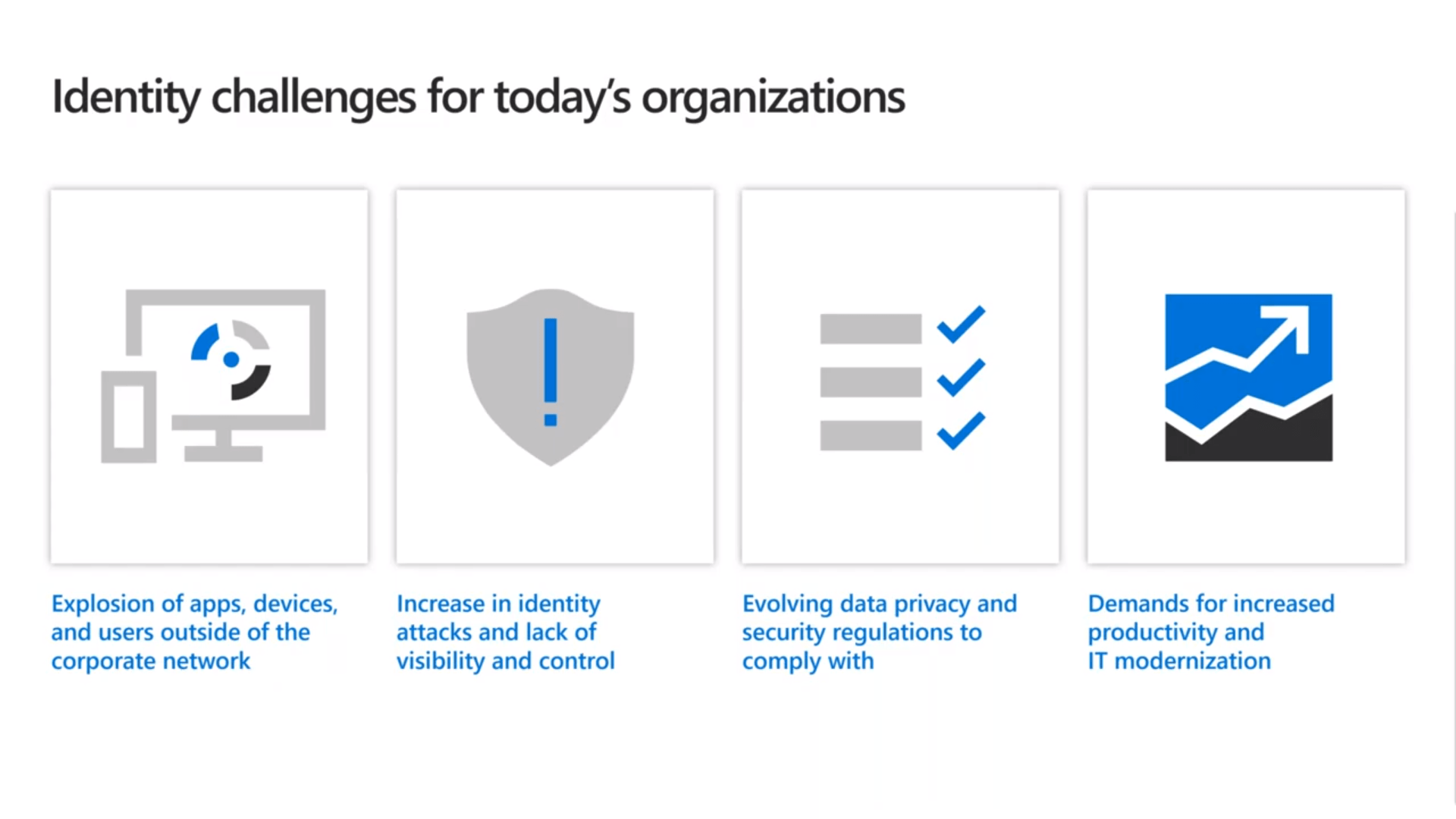
- The explosion of apps on-premise and BYOD and external users outside your corporate network are coming in, and those could be customers, vendors, partners, contractors, whoever is needing access to collaborate share data. The result of that there’s been an increase in identity attacks, and for most organizations, they lack the visibility and control.
- Increases in identity attacks and lack of visibility and control is leaving organizations vulnerable. Some organizations have protocols in place to watch out for suspicious activity. However, organizations may not have the time to go and proactively review every log. The lack of visibility and control has been a big struggle we have seen for businesses of all sizes.
- Evolving data privacy and security regulations means more challenges for organizations. Major tech companies like Google and Facebook are UPPING their data privacy and security regulations. General Data Protection Regulation (GDPR) is a regulation on data protection and privacy for all individual citizens. These new regulations will mean updated compliances that organizations will have to follow.
- Demands for increased productivity and IT modernization place a heavy workload on IT departments. With all the changes happening we have changed how we work. Mobile working is continuing to increase. The modernization of IT, having self-service access has also lead to more demands by users.
Identity is the New Control Plane
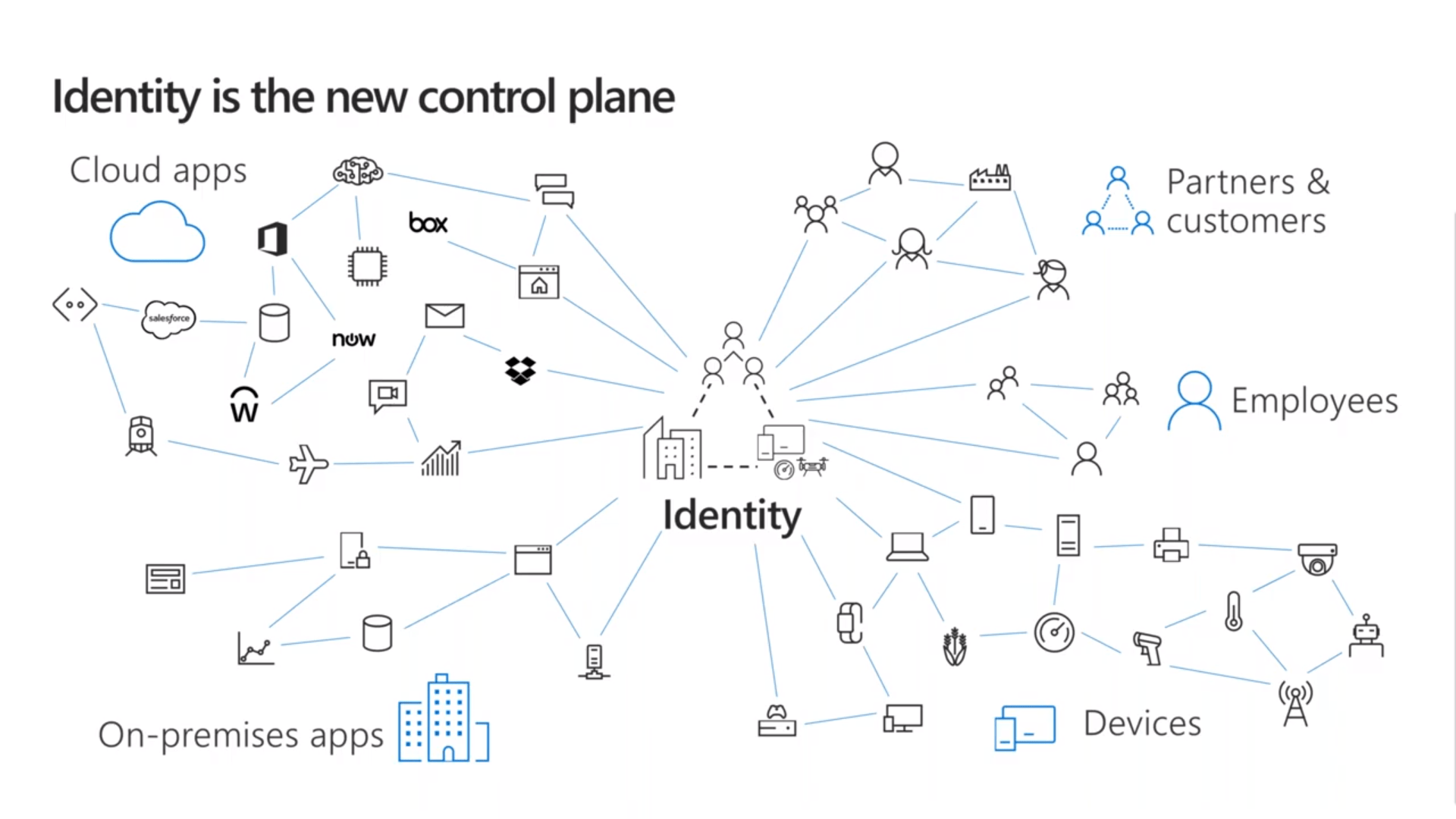
In the current IT and business environment, we are looking at identity as the new control plane. In the above graphic, you can see it doesn’t matter if you’re an employee, a partner, or a customer, if you’re trying to access cloud or on-premise applications regardless of what device you’re using the universal commonality is no longer the physical location; it’s the identity.
Seamless Access to Apps
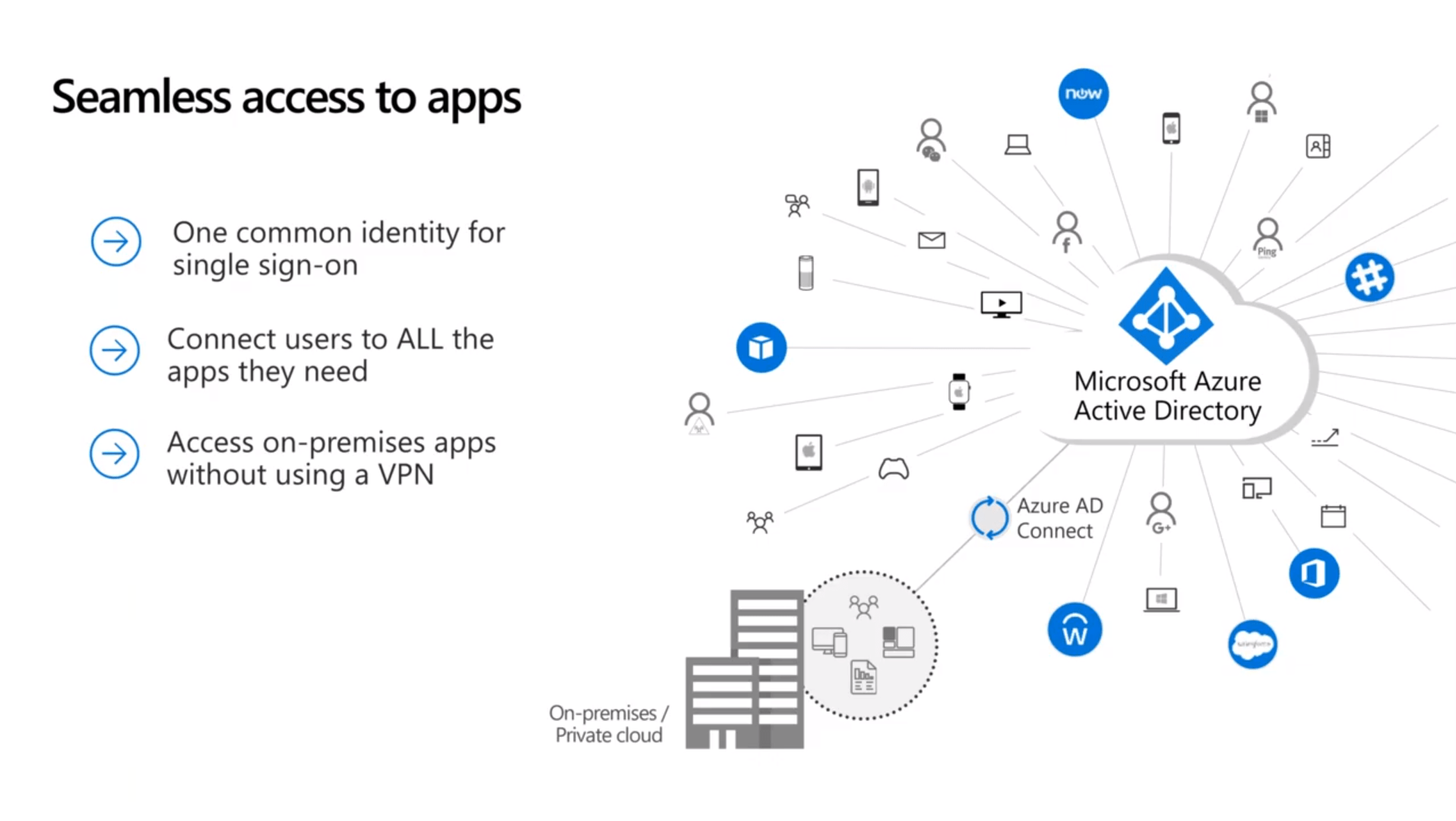
Most customers already have on-premise investments in Active Directory, with Azure AD Connect we can synchronize them. If you’re already using Office 365, you’re more than likely continuing to use this. As a result, we have one collective identity that you’ve made investments in that extends to the cloud. Red Level can provide single sign-on to a tremendous amount of applications, and depending on your on-prem applications, we might be able to deliver access to those without needing to use a VPN.
Safeguard User Credentials with a Zero Trust approach
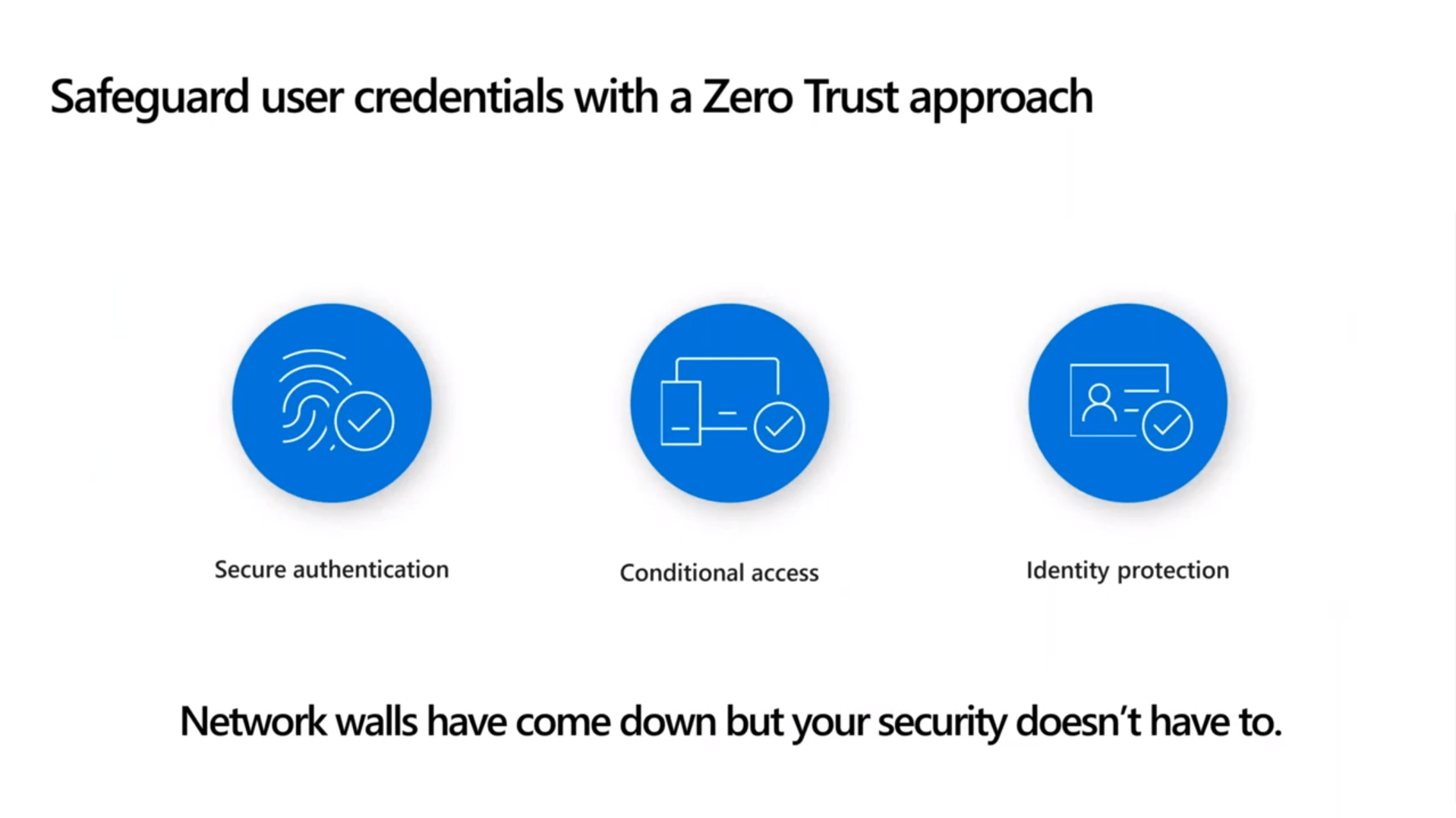
From a security standpoint, it’s all about safeguarding your user credentials with a Zero Trust approach. We do that to have secure authentication, conditional access, and identity protection. We are moving away from the castle and moat model that IT once used. We have employees that are out in the field and external resources coming in and out of our environments, modern collaboration, and data sharing. Just because the network is changing and walls are coming down, doesn’t mean you have to give up security, nor should you.
Secure Authentication using MFA

When we look at multi-factor authentication (MFA) as a way of providing better protection for identity, Microsoft research shows that organizations that utilize MFA reduce the chance of an attack by 99.9%. The most commonly used form of MFA is the Authenticator app on your mobile device. You can also use Voice, Call or SMS. There are a few new things like the UV keys for OATH codes.
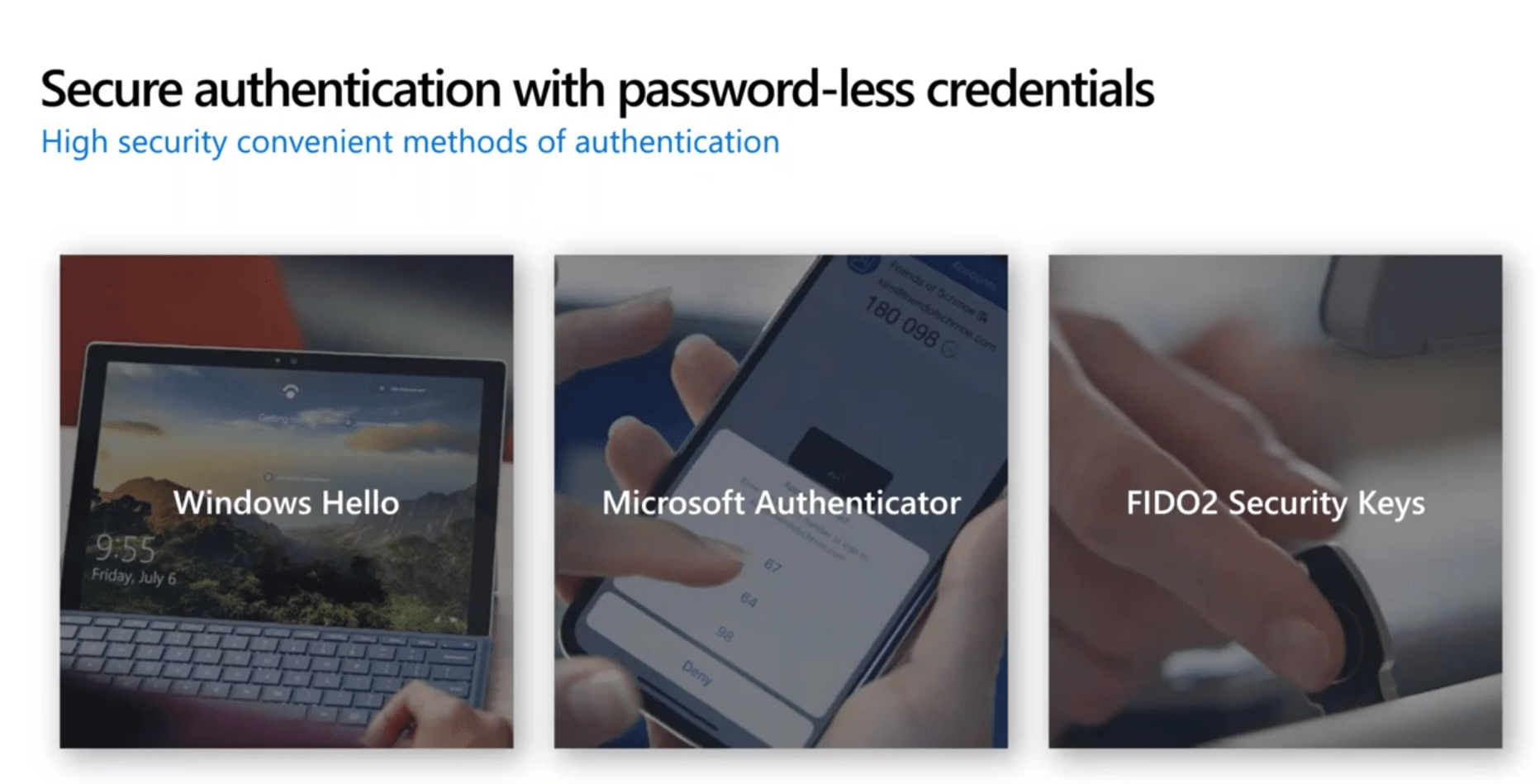
For those ready to ditch passwords altogether, we can move to password-less credentials using technologies like the Windows Hello for Business, Microsoft Authenticator, and FIDO2 security keys.
Conditional Access
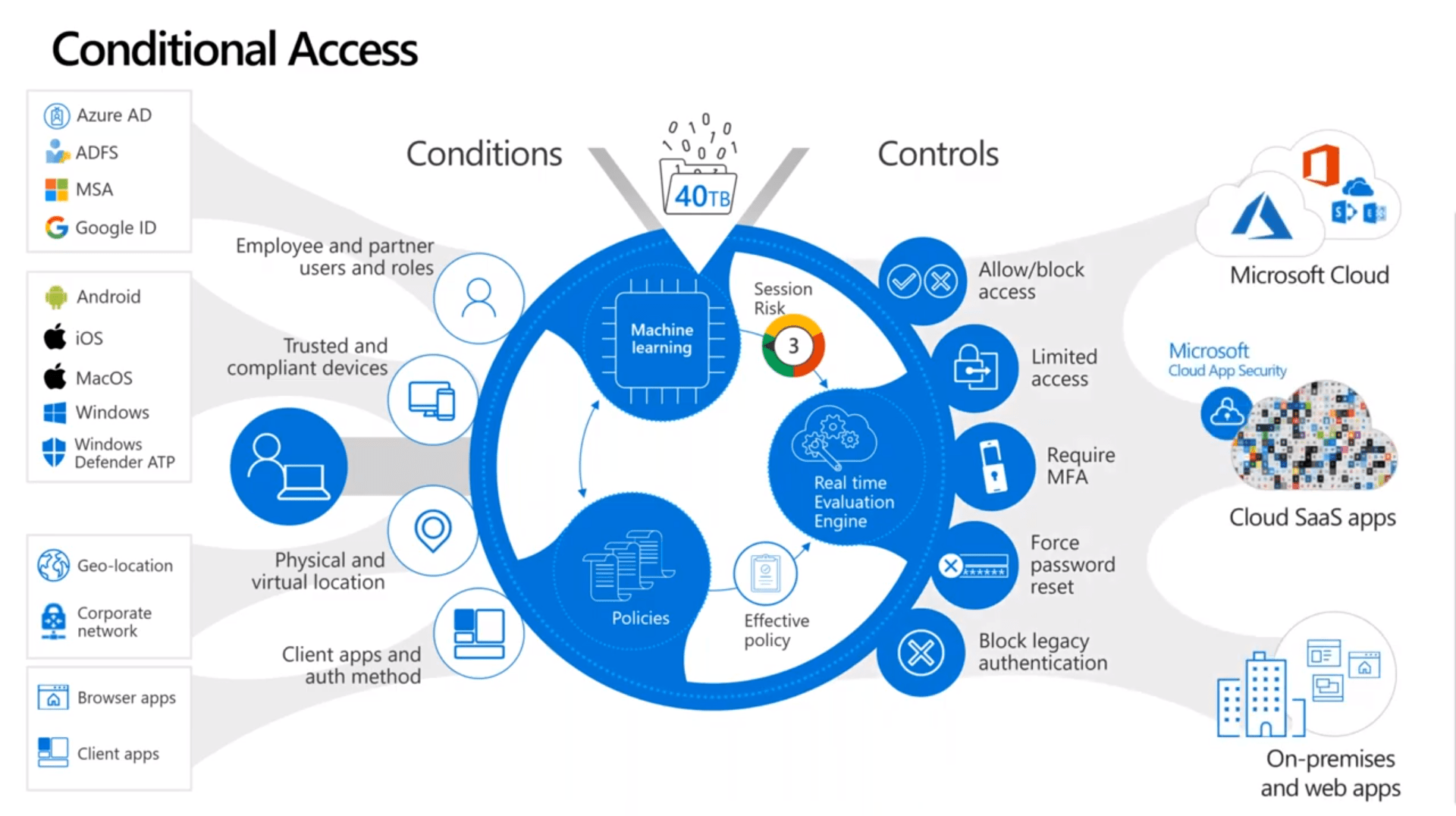
How do we make sure that security is balanced with user experience? We all have these conditions on the left-hand side in the above graphic that we can create policies around. We can leverage Microsoft’s rich database of security intelligence and use machine learning and behavioral analytics to make sure that we’re proactively using that data to determine what a risk might be. Lastly, create the right controller to allow access to your Microsoft cloud apps third-party SAS apps, on-premise, web apps that are supported.
Want to make sure your organization is secure? Our Microsoft 365 Security Workshop will give you a prioritized and actionable security roadmap for your organization.
For more information about gaining a competitive advantage with digital transformation, contact Red Level today.
Related Posts
Picture this: it’s a Tuesday morning in October.You’re halfway through ...
Windows 10 End of Support is Coming Microsoft is officially ...
Microsoft is enhancing SharePoint to help organizations create more engaging ...