While an attack on your organization may not create global headlines, the impact to your organization and its’ employees could be devastating. If it extends to your customers’ information and records, it could negatively impact them and shatter your reputation.
That’s what I saw when I put my last name and the last 6 digits of my SSN in the website Equifax set up after the breach was publicly announced. I’m not overly surprised. I had a nearly 50% chance of being one of the 143,000,000 Americans impacted by the attack. Just a flip of the coin and now I’ll likely have to worry about identity theft for years to come.
The difference between the Equifax breach and the largest known cyber breach in history (remember Yahoo between 2013-14 and the 1.5 billion user accounts?) is that this one is the holy grail. The whale of whales. It includes the key ingredients (e.g. Social Security numbers, birth dates, addresses, and in some cases, driver’s license numbers) to perform identity theft on roughly half of the U.S. population. For an even unluckier 209,000 consumers, it also included credit card information and dispute documents with personally identifying information (PII) for another 182,000.
As I researched the breach and began drafting this blog post, I had a sobering moment and a quote hit me from one of my all-time favorite movies.

It’s a powerful scene from what I think is one of the all-time great movies: The Shawshank Redemption. Now, I’m nowhere near Brooks’ age in the movie but I’ve seen the rapid evolution of technology and the impact it has had on our way of life. Technology is only going to expand its presence in our lives (think IoT, wearables, cloud computing). As a result, cyber attacks will continue and only become more complex. The risk is real and the chance you will be attacked is very high.
The cost of cybercrime to the global economy is estimated to reach $8 trillion by 2022.
I think the biggest misconception among non-IT (security) professionals is what hackers do in a “hack”. Don’t let Hollywood fool you. It’s rarely super introverted, pale-skinned men in a dark basement looking to wreak havoc. Modern hackers look like you and me, have families, and live all over the world. Their motive is becoming overwhelmingly financial. According to Ann Johnson, Microsoft’s Vice President of Enterprise Product & Cybersecurity Groups, the cost of cybercrime to the global economy is estimated to reach $8 trillion by 2022.
What may also surprise you (thanks again to Hollywood) is that most hackers are opportunists waiting for your employees to make a mistake – not slamming their keyboard at 200 words per minutes typing sophisticated looking scripts and commands to “break into the system” in real-time. The most common examples include falling victim to a phishing email or opening an unsafe file attachment. It’s also becoming a lot more common for hackers targeting specific organizations to be more proactive and use “social engineering” techniques to trick your employees into thinking the fake email or malicious attachment are genuine.
Once inside, they’ll typically follow what’s known as an advanced persistent threat, or APT, which is a set of stealthy and continuous computer hacking processes (see attack chain image below). The first attack starts with the goal of identifying interesting assets and learning more about the environment (e.g. users, devices, servers). They’ll continue until they’re able to obtain administrative credentials (shifting to the yellow area below) to continue the attack, take over other machines, and then run remote code on other machines using the stolen credentials.
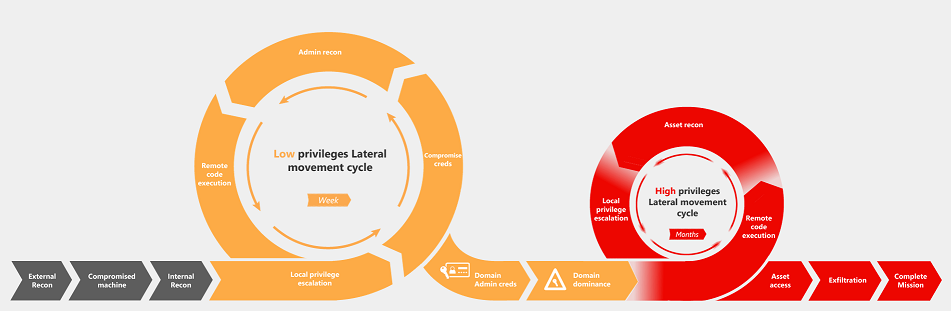
When the attack moves to the red, the attackers typically have full control over the environment (or at least the high-value system they’re looking to break into) and the goal shifts to obtaining the data they’re after. In most cyber breaches, you won’t even realize you’ve been attacked until the mission is complete and the attacker is long gone – if you even find out.
So, how easy is it for a hacker to get control of a system? Watch this short video produced by CNN Money on how an ethical hacker was able to obtain access in under 2 minutes:
It can’t be that easy, can it? Here’s another great video of how easy it is to use social engineering was back in January 2015 after the Sony cyber breach (10th largest in history) when Jimmy Kimmel and his team asked random individuals what their actual passwords were on the street in Los Angeles:
Need help preventing a cyber-attack? Red Level is here to help. Call 248-812-8200
Originally posted on LinkedIn.
For more information about gaining a competitive advantage with digital transformation, contact Red Level today.
Related Posts
Windows 10 End of Support is Coming Microsoft is officially ...
As we celebrate our 20th anniversary at Red Level, we're ...
Data breaches are becoming alarmingly common. The recent "Mother of ...