Out with the old. Preview the new.
Happiness is cleaning the junk out of your server room and knowing you’re up-to-date on the latest software. At Tech Spring Cleaning, you’ll get both plus a tasty lunch and a chance to win a new laptop. Join your friends at Red Level and C/D/H for our annual Tech Spring Cleaning event.
Bring us your old servers, hard drives, and computers for safe and secure recycling. Make sure you’re up-to-date as several key technologies (SQL Server 2008, Windows Server 2008, Windows 7) hit end-of-life.
April 10th
Grand RapidsWest Michigan Works
215 Straight Ave NW
Grand Rapids, MI 49504
Wednesday, April 10th
11am – 1pm
April 11th
Metro DetroitRed Level Tech Center
40200 Grand River
Novi, Michigan 48375
Thursday, April 11th
11am – 2pm
RSVP for the Tech Spring Cleaning 2019
Clear out the clutter in your server room and learn about new business-grade technologies that will spring your team forward at Red Level’s annual Tech Spring Cleaning event.

Honors and Awards
We’re committed to doing our very best for every client, every day. But you don’t have to take our word for it. Red Level is fortunate to be honored by major publications, suppliers, and community organizations:

RCP Top 200 Microsoft Partner &
3-Time Microsoft Partner of the Year

6-Time Inc 5000 of America’s Fastest Growing Companies

Crain’s Cool Places to Work and
Metro Detroit’s 101 Best & Brightest

CRN Tech Elite 250, CRN MSP 500
and CRN Pioneer 250
The latest news from Red Level
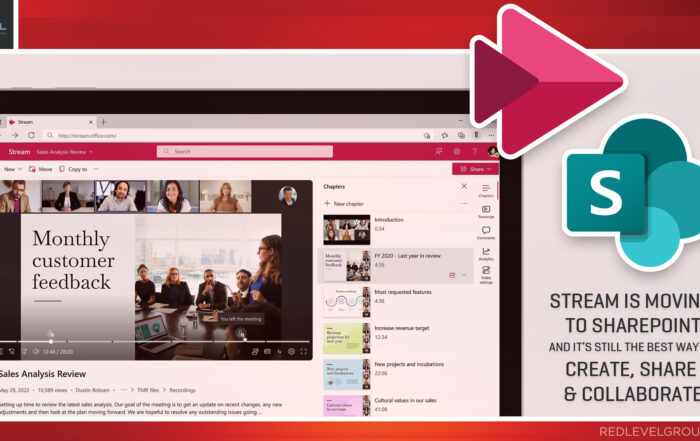
Transition from Stream (Classic) to Stream (on SharePoint): A Comprehensive Guide
Significant changes are on the horizon for users of Microsoft Stream, the video management solution within the suite. Effective April 15, 2024, Microsoft will retire Stream (Classic) to Stream (on SharePoint). This transition is not just ...
Red Level Recognized as a Best Places to Work in Technology
We are thrilled to announce that Red Level has been named as one of the Best Places to Work in Technology for 2024. This distinguished award, presented by Best Companies Group, is a testament to ...
Red Level Recognized on CRN’s 2024 Managed Service Provider 500 List
CRN®, a brand of The Channel Company, has named Red Level to its Managed Service Provider 500 list in the Pioneer 250 category for 2024. The MSP 500 list compiled by CRN serves as a comprehensive ...